While most people are familiar with email phishing scams, a more insidious form of attack has been gaining momentum: smishing. This comprehensive guide explains everything you need to know about SMS phishing attacks and how to protect yourself from becoming a victim.
What is Smishing?
"Smishing," a portmanteau of "SMS" and "phishing," is a form of cyber attack in which criminals use fraudulent text messages to trick recipients into taking actions that compromise their personal and financial information. Like traditional phishing, smishing exploits social engineering techniques to manipulate victims into clicking malicious links, sharing sensitive data, or downloading harmful software.
According to the Federal Communications Commission (FCC), smishing has become increasingly prevalent as people rely more heavily on their mobile devices for personal and business communications. The name combines "SMS" (Short Message Service) with "phishing" to describe this text-based version of one of the internet's oldest and most successful scams.
Why Smishing is Particularly Dangerous
Text messages have an open rate of approximately 98%, compared to just 20% for emails. Studies show people respond to 45% of their text messages while only 6% of emails receive a response. This higher engagement rate, combined with the fact that most people keep their phones within reach at all times and typically read texts within minutes of receipt, makes smishing an extremely effective attack vector for cybercriminals.
How Smishing Attacks Work
Smishing attacks operate through a simple but effective process:
- Message Distribution: Attackers send text messages to thousands of phone numbers, often obtained through data breaches or purchased from illicit sources.
- Impersonation: The messages appear to come from trusted entities such as banks, government agencies, delivery services, or well-known companies.
- Creating Urgency: Messages typically contain urgent calls to action, threatening consequences for inaction or promising rewards for immediate response.
- Harvesting Information: If recipients click on included links, they are directed to fraudulent websites designed to steal login credentials, personal information, or payment details.
- Malware Installation: Some smishing attacks aim to install malware on the victim's device, which can steal data, track activity, or even take control of the device.
Common Smishing Tactics and Scenarios
The Department of Veterans Affairs and the FCC have identified several prevalent smishing scenarios that everyone should be aware of:
Financial Institution Impersonation
Messages claim to be from your bank or credit card company, alerting you to:
- Suspicious account activity or unauthorized login attempts
- Problems with payment information requiring immediate verification
- Account suspensions that need to be addressed immediately
- Expired credentials that must be updated
Package Delivery Notifications
With the rise of e-commerce, delivery notification scams have become extremely common:
- Messages claiming a package couldn't be delivered
- Notifications about unexpected packages requiring address confirmation
- Requests to reschedule delivery by clicking a link
- Alerts about shipping fees that must be paid
Government and Tax Authority Impersonation
The FBI has specifically warned about an increase in IRS-related smishing scams:
- Messages claiming you're eligible for a tax refund
- Threats about tax delinquency or legal action
- Notifications about economic stimulus or relief payments
- Requirements to verify your identity to receive government benefits
Prize or Giveaway Notifications
Appeals to greed are particularly effective:
- Messages stating you've won a lottery or sweepstakes
- Notifications of gift cards or rewards from retailers
- Offers of free products or services requiring "verification"
- Exclusive discount codes available for a limited time
Technical Support Scams
These prey on people's concerns about device security:
- Alerts about malware or viruses detected on your device
- Warnings about account security breaches
- Notifications about subscription renewals for security services
- Messages claiming your device needs an urgent security update
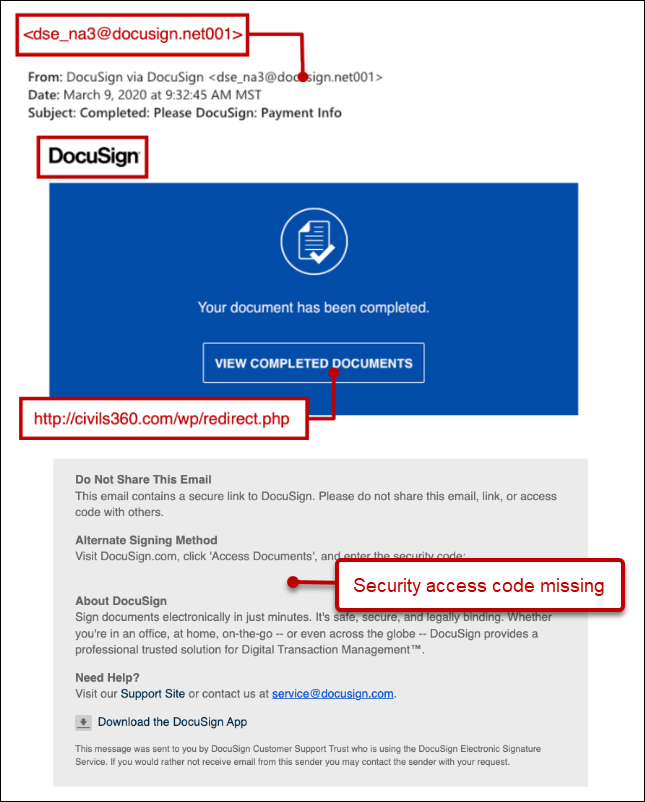
Real Example of a Smishing Text
"ALERT: [Bank Name] has detected unusual activity on your account. To prevent unauthorized access, verify your identity at: hxxp://bank-secure-verify.com/login"
This example shows classic smishing elements: creating urgency through an "alert," impersonating a trusted institution, and providing a suspicious link with a domain name designed to appear legitimate.
How to Identify Smishing Attempts
Based on guidance from the FCC and Bank of America, here are key warning signs that a text message may be a smishing attempt:
- Urgent or threatening language - Messages that create a sense of urgency or fear are designed to make you act quickly without thinking.
- Unexpected texts requesting personal information - Legitimate organizations rarely request sensitive information via text message.
- Suspicious links - Be wary of shortened URLs (like bit.ly or tinyurl.com) or links with slight misspellings of legitimate domains.
- Generic greetings - Messages starting with "Dear Customer" instead of your name may indicate a mass-distributed scam.
- Grammar and spelling errors - Professional organizations typically have quality control processes for their communications.
- Offers that seem too good to be true - Promises of free money, prizes, or unrealistic discounts are common lures.
- Requests to verify account information - Legitimate companies don't typically ask you to provide or verify sensitive information via text.
- Messages asking you to call an unfamiliar number - Some smishing attacks direct victims to call a number where scammers pose as customer service representatives.
- Suspicious area codes - Be cautious of texts from area codes you don't recognize, especially international numbers.
- Requests to download apps or files - These could contain malware designed to compromise your device.
Smishing Protection Strategies
Preventive Measures for Individuals
- Never click links in suspicious texts - If you need to check account status, type the official website address manually in your browser.
- Don't respond to unknown senders - Even replying "STOP" confirms your number is active and may lead to more spam.
- Block and report suspicious numbers - Most carriers allow you to forward suspicious texts to 7726 (SPAM) to report them.
- Keep your device's operating system updated - Security patches help protect against known vulnerabilities.
- Install security software on your mobile device - Anti-malware apps can provide an additional layer of protection.
- Use multi-factor authentication - This adds an extra layer of security to your accounts.
- Verify through official channels - If you're concerned about a message, contact the company directly using their official website or phone number.
- Be skeptical of unexpected messages - If you weren't expecting a text about a delivery, prize, or account issue, be extra cautious.
For Organizations
- Implement employee awareness training about smishing
- Establish clear procedures for reporting suspicious messages
- Consider mobile device management (MDM) solutions for company devices
- Develop and communicate policies about sharing company information
- Implement secure channels for sensitive communications
- Conduct regular smishing simulation exercises
What to Do If You've Been Smished
If you believe you've fallen victim to a smishing attack, take these immediate steps:
- Change compromised passwords immediately - Update passwords for any accounts that may have been affected.
- Contact financial institutions - If you've shared banking or credit card information, notify your financial institutions immediately.
- Enable additional security measures - Add two-factor authentication to vulnerable accounts.
- Monitor accounts for suspicious activity - Check your accounts regularly for unauthorized transactions.
- Report the incident - Notify the organization that was impersonated, the FCC, and the Federal Trade Commission (FTC).
- Run a malware scan - Check your device for any malicious software that may have been installed.
- File a police report - If you've experienced financial loss, consider filing a report with local law enforcement.
Emerging Trends in Smishing Attacks
As defenses improve, smishing techniques continue to evolve:
- Conversational Smishing - More sophisticated attacks engage victims in ongoing conversations to build trust before delivering the malicious payload.
- QR Code Smishing - Instead of traditional links, attackers use QR codes that, when scanned, lead to malicious websites.
- AI-Generated Content - Artificial intelligence is being used to create more convincing and personalized smishing messages.
- Multi-Platform Attacks - Sophisticated campaigns coordinate across SMS, email, and phone calls to create more convincing scams.
- Exploitation of Current Events - Attackers quickly adapt to global events, creating smishing campaigns around disasters, pandemics, or economic issues.
Smishing by the Numbers
11,954
Smishing attempts reported to the FCC in 2023 alone
138%
Higher open rate for text messages compared to emails
700%
Increase in non-email phishing attacks (including smishing) in Q2 2022
$1.4+ Billion
Losses to Americans from cybercrime in 2023, with a significant portion attributed to phishing and smishing
Conclusion
Smishing attacks represent a significant and growing threat in our increasingly mobile-dependent world. The combination of high engagement rates for text messages and sophisticated social engineering techniques makes these attacks particularly effective. However, by staying informed about common tactics, maintaining healthy skepticism toward unexpected messages, and following best practices for mobile security, you can significantly reduce your risk of becoming a victim.
Remember that legitimate organizations will never ask for sensitive information via text message. When in doubt, don't click links or respond to the message. Instead, contact the purported sender through their official channels to verify the communication's authenticity.
As smishing techniques continue to evolve, staying educated about the latest threats and maintaining vigilant digital habits remain your best defense against these sophisticated scams.
Further Resources
- What is Phishing? The Complete Guide to Identifying and Preventing Attacks
- Real-World Smishing Examples: Case Studies and Analysis
- How to Protect Your Business from Phishing Attacks
- The Role of AI in Modern Scam Detection
- FCC: Avoid the Temptation of Smishing Scams
- VA.gov: Smish, Smish! Don't get phished
Get Protected with Scam Helper
Not sure if a text message is legitimate? Scam Helper is your second opinion for suspicious messages. Our platform uses advanced AI to analyze text messages for signs of smishing, providing real-time protection against sophisticated scams.
When in doubt, don't click—check with Scam Helper first. Our technology can identify even the most convincing smishing attempts.